Home > News > Media News > Detail
According to a recent global market research report released by the independent research firm Harris Poll, over 77% of surveyed enterprises have already adopted a hybrid cloud architecture. However, most of the surveyed enterprises also struggle with the complexity of collaborative work in a multi-cloud environment. The report further noted that due to skill gaps, insufficient security capabilities, and compliance constraints, most enterprises may have blind spots that expose their data to risks due to these challenges.
Microware's Senior Consultant, Ma Kwok-fai, stated: "It is relatively simple to follow company policies for traditional deployments, but extending security policies to public locations poses many obstacles. How to provide an enterprise-grade environment for employees on untrusted networks is a pain point for many local companies. Facing the post-pandemic hybrid work model, SMEs may not have sufficient technical expertise and manpower to handle this transition and struggle to keep up with the rapid market changes. This is why Microware and Check Point have partnered to provide new solutions specifically tailored for hybrid environments, to help SMEs quickly deploy their transformations."

▲Microware's Senior Consultant, Ma Kwok-fai, frankly stated that with the widespread adoption of the hybrid work model in the new normal, it has become much easier to drive enterprises to implement Zero Trust.
Ma Kwok-fai acknowledged that in the past, when employees were seated in the office, small and medium-sized enterprises rarely considered changing their security deployments, making it quite difficult to promote the best practices of Zero Trust. However, as the second wave of the pandemic became increasingly severe, enterprises began to encounter various problems, such as which applications must be exposed to remote users and how to configure user permissions in a hybrid work model. As a result, it has become increasingly evident that more and more enterprises are adopting Zero Trust.

▲Check Point's Cybersecurity Engineering Director for Hong Kong and Taiwan, Hau Ka-chun, emphasized that a unified security policy is crucial for a hybrid work environment spanning different platforms.
Check Point's Cybersecurity Engineering Director for Hong Kong and Taiwan, Hau Ka-chun, believes that many local enterprises have recognized the importance of Zero Trust, and even have plans to implement it, but face numerous challenges in the actual execution.
"In Hong Kong, everyone has the concept of Zero Trust, but the deployment rate is not as high as expected. After all, whether the enterprise's infrastructure can support Zero Trust, as well as the investment required to move towards a Zero Trust architecture, are big issues. Moreover, the shortage of manpower is also a major problem. Even if small and medium-sized enterprises have relevant plans, they often have to postpone them due to the lack of personnel," Hau Ka-chun continued.
"The pandemic is an opportunity to drive enterprises towards Zero Trust. In the past, the general practice was to divide the internal and external networks into 'Trust' and 'Untrust' zones, but after the pandemic, there is no longer such a clear boundary, as users have already left the trust zone. This has led enterprises to have a greater demand for Zero Trust, so that employees can work remotely securely from anywhere."
However, he also mentioned that after the pandemic, as Security-as-a-Service has become more prevalent, implementing Zero Trust has become easier for enterprises compared to before. Not only is the pressure on resources significantly reduced, but the process is also much faster.
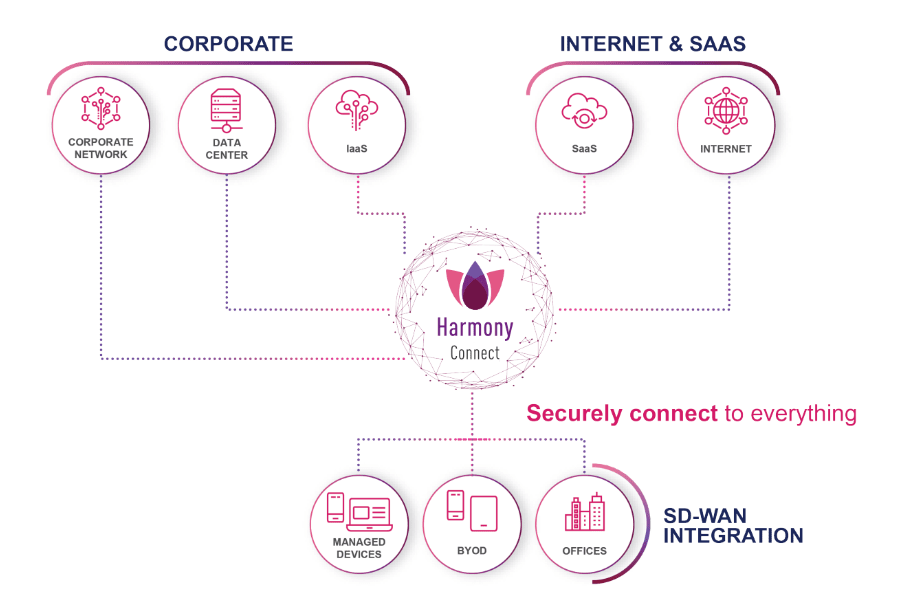
▲HARMONY CONNECT enables enterprise users to securely access the corporate network and all applications remotely.
Ma Kwok-fai revealed that Microware had already partnered with Check Point a year ago, with the latter providing product technology, while Microware is responsible for the full sales, deployment, and support services, deploying the Check Point Harmony solution for enterprises as needed.
The solution covers six areas and can effectively provide comprehensive network security for enterprises:
Hau Ka-chun further explained that if an enterprise is unfortunately breached, the End point solution can also provide Runtime Protection to minimize the impact on infected devices. For example, if an employee accidentally enters a password on a phishing site, the entire malicious activity can be intercepted at different stages. It also provides complete transparency for the enterprise to clearly understand what happened during the attack.
Traditional enterprises often choose security products from different vendors, such as using one vendor for email and another for endpoint security. While this can achieve the same level of security, it presents challenges in daily management, especially when trying to establish a unified security policy. For example, if an AI is used to define phishing website patterns, it can be difficult to ensure consistency across different platforms. In the event of a security incident, investigating across multiple platforms can also be complex and time-consuming.
"For SMEs, their infrastructure is relatively simple, and they hope to undergo a large-scale transformation. However, due to limited manpower and budgets, they generally tend to take a gradual approach from on-premises to the cloud. We chose to partner with Check Point because they can cater to the entire platform, from user, infrastructure, to endpoint, to implement a Zero Trust approach," revealed Ma Kwok-fai. For local SMEs, the entry point is often Harmony Email, as email is the most commonly used application in any company. Next is VPN, as the increasing demand for work-from-home has driven SMEs to deploy it. Since the cost of deploying these three items is not much different from a full solution, enterprises often choose to gradually expand the deployment after trying it out or as their business needs grow.
According to Check Point's "Cyber Attack Trends: 2022 Mid-Year Report", ransomware has had the biggest impact on enterprises. In recent years, as many companies have implemented backups, they can simply restore from backups when hit by ransomware and refuse to pay the ransom. As a result, new ransomware strains no longer simply lock systems, but also aim to steal sensitive data to extort companies.
To address ransomware, Check Point Harmony not only analyzes and blocks malware upfront but also immediately isolates infected data and restores all Snapshot backups if a user is locked by ransomware. It also provides a comprehensive forensic report to help users understand how the security incident occurred.